By Xavier Mesrobian
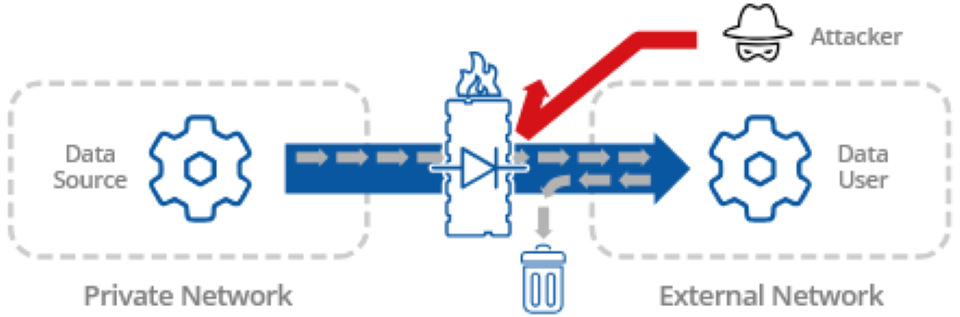
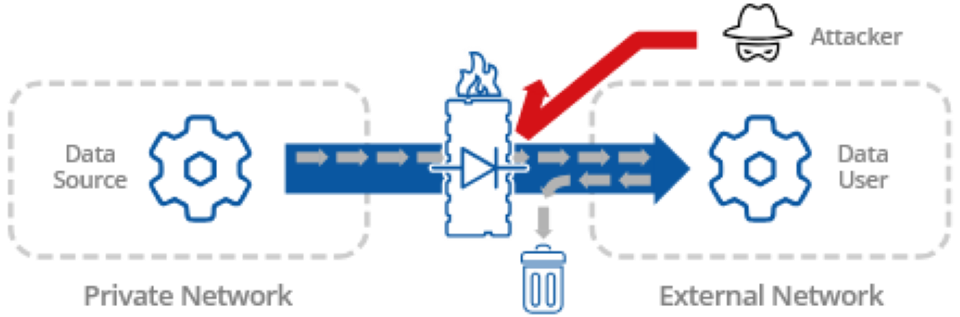
The best way to ensure complete data isolation for a networked OT system is with a data diode. You can send data out and nothing gets in. Not a single TCP packet ever gets delivered, so there is no chance of suspicious or malformed content entering the system.
The question is, how to connect?
No standard industrial protocol connects through a data diode — not OPC UA, MQTT, or any other.
For example, OPC UA uses UDP to traverse a data diode, but UDP is not practical for most industrial applications. The data it delivers may be damaged, out of sequence, or incomplete.
MQTT can connect outbound through a firewall, but it still requires a two-way data flow to send data.
The Best Approach
The best approach is tunnel/mirroring. This encapsulates the data in a special protocol to pass through the data diode and converts it back at the destination.
Because the transaction is one way, not all aspects of the original protocol are maintained. Synchronous transactions become asynchronous, and the server state may not be perfectly mirrored. But a tunnel/mirror connection maintains all the essential information across the tunnel: point names, values, timestamps, and quality information, and replicates it on the other side, with no loss of data.
What’s more, a well-designed tunnel/mirror system can provide additional advantages:
- Guaranteed consistency of data
- Support for a universal namespace
- Store and frowarding
- Data path redundancy
Other Options
Of course, it might not always be practical or feasible to implement a hardware data diode. In those cases, you can still gain significant benefits through a tunnel/mirroring approach if your software can emulate a data diode. This would discard any incoming application data without being processed, so a compromised receiver could not attack the data source. And it could support SSL if necessary, which a hardware data diode cannot do.
A less secure but still very practical use case is to configure a tunnel/mirror connection to make only outbound connections. This keeps all firewall ports closed but allows two-way data flow for writing back to the system.
It can also be made fully compatible with a DMZ to provide protection to both the OT side and the recipient side of the connection.
Whatever option your budget and circumstances allow, a good tunnel/mirroring package like Cogent DataHub software from Skkynet offers practical solutions.
To protect OT systems that need two-way data flow, you can keep all inbound firewall ports closed and connect via DMZ if needed.
And even if your company requires a data diode, shutting down all incoming data packets should not restrict your options.
DataHub tunnel/mirroring lets you choose the protocol of the data feed for source and client in a universal namespace, and offers store and forwarding, data path redundancy, and a way to guarantee data consistency.
Xavier Mesrobian is on the board of directors at Skkynet Cloud Systems.
This content is sponsored by Skkynet.
*Featured Image courtesy of Skkynet