By Xavier Mesrobian
How can you implement Industrial AI and also keep your customer’s OT data secure? The optimal approach, mandated by the NIS2 Directive and NIST CSF 2.0, is complete network segmentation.
The OT system should be fully isolated from the Internet and any cloud system. This is best done using a DMZ (demilitarized zone), keeping the production network behind closed firewalls. The question is, how?
Protocol Challenges
Moving production data to a cloud-based AI system in real time through a DMZ requires two steps, plant-to-DMZ and DMZ-to-cloud.
However, the two most popular industrial protocols, OPC UA and MQTT, were not designed for this.
The OPC UA protocol is too complex to reproduce well in a daisy chain across multiple servers. Information will be lost in the first hop. The synchronous multi-hop interactions needed to pass data across a DMZ would be fragile on all but the most reliable networks and would result in high latencies.
MQTT can be daisy-chained, but it requires each node in the chain to be individually configured and aware that it is part of the chain. The QoS (Quality of Service) guarantees in MQTT cannot propagate through the chain, making data at the ends of the chain unreliable.
Therefore, MQTT is best used as the last step only, to move data from the DMZ to the cloud.
The problem remains, how to move data securely from the plant to the DMZ? OPC UA would require opening a firewall on the production network, which is too high a risk. Most security administrators will simply not allow it.
Tunnel/Mirroring
Since neither OPC UA nor MQTT alone, or together, are sufficient for passing data through a DMZ, another approach is needed — one that integrates well with both of these protocols.
Secure tunnel/mirroring software provides a solution. It can make the connections at both ends and pass the data along the daisy-chained connections through a DMZ.
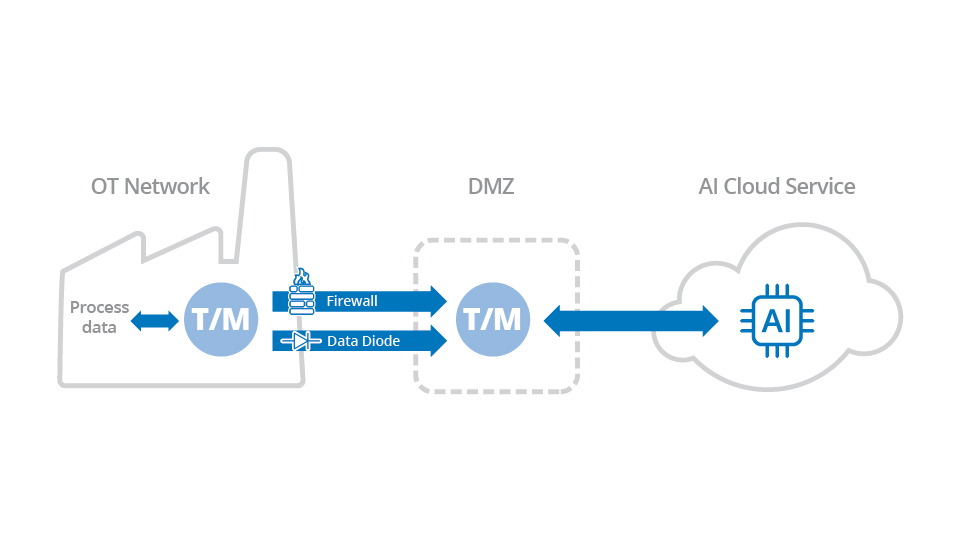
The tunnel/mirror software connects to MQTT, OPC UA, or other industrial protocol at the production facility and mirrors the full data set to a similar component on the DMZ.
Ideally, both components should be able to maintain the data in a unified namespace. This way the data can be converted to MQTT for sending to the AI cloud service from the DMZ.
The mirroring capability of the tunnel/mirror software keeps that data consistent between the original data source, the DMZ, and the AI system.
Firewalls and Data Diodes
Since all inbound firewall ports on the production system must be kept closed, the tunnel/mirror system must be able to make outbound-only connections to the DMZ.
Also, some mission-critical applications require a hardware data diode to ensure that not a single data packet gets back to the industrial network. The tunnel/mirror system would need to provide data diode support for that level of secure architecture.
Other AI implementations may call for bidirectional data flow. The tunnel/ mirror technology should be flexible enough to support that, if needed.
In any case, there should be no access to data beyond what the AI system uses. Plant engineering staff must have full control over which data will be made available.
Many companies today are looking at industrial AI to optimize production.
But they need secure access to production data. This is difficult, but not impossible.
You can protect an OT network with a DMZ and still feed data to AI systems, using secure tunnel/mirroring.
Cogent DataHub software from Skkynet provides an off-the-shelf tunnel/mirror solution that is DMZ and data diode compatible and keeps all inbound firewall ports closed.
Xavier Mesrobian is on the board of directors at Skkynet Cloud Systems.
This content is sponsored by Skkynet.
*Featured Image courtesy of Skkynet